Hi All,
Sorry for the break in blogs about monitoring – I’ve been quite busy with work, so I haven’t had the time to create a monitoring blog. I have been able to create a blog about deploying Always-on VPN, or as Microsoft used to call it “Auto-VPN”. Always-on VPN is going to be the replacement for DirectAccess. DirectAccess was a technology that created 2 hidden VPN tunnels over SSL and encrypted all the data between your client machine and your local network. The downside was that it required Windows Enterprise.
Warning: Long read 🙂
Now with Always-on VPN you no longer need Windows enterprise. The requirement list has changed to only the following:
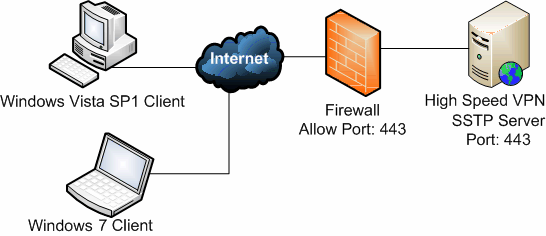
Jun 24, 2021 SSTP is a mechanism to encapsulate Point-to-Point Protocol (PPP) traffic over an HTTPS protocol, as specified in RFC1945, RFC2616, and RFC2818. This protocol enables users to access a private network by using HTTPS. The use of HTTPS enables traversal of most firewalls and web proxies. There are two parts we need to take into consideration, which setup a Secure VPN (SSTP) on Windows Server 2019 and the VPN client configuration on client operating systems such as Windows 10. On the outset, while we talk about Windows servers and Clients, we can also use this step by step guide to install VPN services on Windows Server 2016.
Client:
Windows 10 1607 (Any SKU)
Aug 03, 2020 SSTP-CLIENT - Background: SSTP is Microsofts Remote Access Solution (RAS) for PPP over SSL. It can be used instead of PPTP or L2TP, and is only available with Windows Vista/7 connecting to a Windows 2008 Server. G) Password.Enter your EarthVPN VPN password.Please keep in mind that earthvpn client area and vpn login details are different. H) Click Save icon. Step:4 Click on newly created vpn connection EarthVPN London SSTP and click connect icon. Setup a Client to Connect Step 1. Log into a Windows machine. SSTP was introduced in Windows Vista, so the OS must be Vista or Greater (or Server 2008 and greater). Go to Network and Sharing Center. Click Setup New Connection or Network. Click Connect to a workplace.
Now that is a brief list huh?! I was surprised when I saw that all it needs is a fairly recent windows version. There is one small caveat: for Device based tunnels, instead of user-based tunnels you will require update 1709 too.
In our lab we’ll be configuring a single Windows Server 2016 DC with RRAS and Always-on VPN via SSTP, the server will have a single NIC configuration.

Disclaimer
Before we start I’d like to note that it is always better to separate roles, you do not want your actual domain controller to be a VPN-endpoint and as thus I take no responsibility for security related issues to this blog. I will however try to keep all other best practices in place.
Server side
For our server we will need to have it running as a domain controller already. I assume if you’re reading this blog you already have it set-up, ready, and waiting 😉 one other prerequisite is having a trusted SSL certificate installed for our SSTP VPN, if you don’t want to pay for a certificate for your lab you can use this link or any other free SSL/Letsencrypt certificate provider.
When we have everything ready, we can move on. To make sure we have everything we need:
Install
- Active Directory Domain Services
- Active Directory Certificate Services
- Remote Access with the “DirectAccess and VPN” option selected
Make sure we have:
- A trusted certificate that is already installed
- The domain controller completely configured and ready for use
- A Security group (VPN Users) that includes a test user account
- A test client computer in the domain
- One empty temporary Security Group
Next stop: Getting started with SSTP
When you’ve installed the pre-requisites above we can run the Remote Access Wizard and choose the option “Deploy VPN and DirectAccess” we do this to ease the installation of SSTP, it configures NPS for us and creates the SSTP listeners. After finishing setting up the DirectAccess external URL in the Wizard click on the Edit option that is presented to you. Move the “DirectAccess settings will be applied to all mobile computers in security groups” security group to our temporary group.
Click Finish and have the DirectAccess configuration setup complete. immediately after finishing the Wizard we can go to the Group Policy Management console and delete the DirectAccess Group Policy objects before they ever apply – by doing this we remove the configuration of DirectAccess but keep our SSTP VPN intact.
GPO’s
Next up is creating a group policy so certificates will be enrolled automatically, this is all from Microsoft’s guide directly with some minor edits to make the entire picture a bit more clear:
• Open GPO management
• Create a new policy at the root level called “Certificate Auto-Enroll”
• Computer Policy:
o Computer ConfigurationPoliciesWindows SettingsSecurity SettingsPublic Key Policies.
o Certificate Services Client – Auto-Enrollment: Enabled
o Select “Renew expired certificates”, “update pending certificates”, and “remove revoked certificates” and “Update certificates that use certificate templates.”
• User Policy:
o User ConfigurationPoliciesWindows SettingsSecurity SettingsPublic Key Policies.
o Certificate Services Client – Auto-Enrollment : Enabled
o Select “Renew expired certificates”, “update pending certificates”, and “remove revoked certificates” and “Update certificates that use certificate templates.”
• Close GPO management
Certificate Management: User Certificates

• Open Certificate Authority, right click Certificate Templates and click on Manage
• Find “user” in the list of certicates, right click and select “Duplicate”
• On the Properties of New Template dialog box, on the General tab, complete the following steps:
o In Template display name, type VPN User Authentication.
o Clear the Publish certificate in Active Directory check box.
• On the Security tab, complete the following steps:
• . Click Add.
o On the Select Users, Computers, Service Accounts, or Groups dialog box, type VPN Users, and click OK.
o In Group or user names, click VPN Users.
o In Permissions for VPN Users, select the Enroll and Autoenroll check boxes in the Allow column.
o In Group or user names, click Domain Users, and click Remove.
• On the Compatibility tab, complete the following steps:
• . In Certification Authority, click Windows Server 2012 R2.
o On the Resulting changes dialog box, click OK.
o In Certificate recipient, click Windows 8.1/Windows Server 2012 R2.
o On the Resulting changes dialog box, click OK.
• On the Request Handling tab, clear the Allow private key to be exported check box.
• On the Cryptography tab, complete the following steps:
• . In Provider Category, click Key Storage Provider.
o Click Requests must use one of the following providers.
o Select the Microsoft Platform Crypto Provider check box.
• On the Subject Name tab, if you don’t have an email address listed on all user accounts, clear the Include e-mail name in subject name and E-mail name check boxes.
• Click OK to save the VPN User Authentication certificate template.
• Close the Certificate Templates console.
• In navigation pane of the Certification Authority snap-in, right-click Certificate Templates, click New, and click Certificate Template to Issue.
• Click VPN User Authentication, and click OK.
• Close the Certification Authority snap-in.
Certificate Management: User Certificates
To configure the VPN Server Authentication template
• In the Certificate Templates console, right-click RAS and IAS Server, and click Duplicate Template.
• On the Properties of New Template dialog box, on the General tab, in Template display name, type VPN Server Authentication.
• On the Extensions tab, complete the following steps:
o Click Application Policies, and click Edit.
o On the Edit Application Policies Extension dialog box, click Add.
o On the Add Application Policy dialog box, click IP security IKE intermediate, and click OK.
o Click OK to return to the Properties of New Template dialog box.
• On the Security tab, complete the following steps:
• . Click Add.
o On the Select Users, Computers, Service Accounts, or Groups dialog box, type VPN Servers, and click OK.
o In Group or user names, click VPN Servers.
o In Permissions for VPN Servers, select the Enroll check box in the Allow column.
o In Group or user names, click RAS and IAS Servers, and click Remove.
• On the Subject Name tab, complete the following steps:
• . Click Supply in the Request.
o On the Certificate Templates warning dialog box, click OK.
• Click OK to save the VPN Server certificate template.
• Close the Certificate Templates console.
• In the navigation pane of the Certification Authority snap-in, right-click Certificate Templates, click New, and click Certificate Template to Issue.
• Click VPN Server Authentication, and click OK.
• Close the Certification Authority snap-in
Installing the VPN server certificate
• On the VPN server’s Start menu, type certlm.msc, and press Enter.
• Right-click Personal, click All Tasks, and click Request New Certificate to start the Certificate Enrollment Wizard.
• On the Before You Begin page, click Next.
• On the Select Certificate Enrollment Policy page, click Next.
• On the Request Certificates page, select the VPN Server Authentication check box.
• Under the VPN Server Authentication check box, click More information is required to open the Certificate Properties dialog box, and complete the following steps:
o Under Subject name, in Type, click Common Name.
o Under Subject name, in Value, type the name of the external domain clients will use to connect to the VPN (e.g., vpn.contoso.com), and click Add.
o Under Alternative Name, in Type, click DNS.
o Under Alternative Name, in Value, type the name of the external domain clients will use to connect to the VPN (e.g., vpn.contoso.com), and click Add.
o Click OK.
• Click Enroll.
• Click Finish.
• In the Certificates snap-in, under Personal, click Certificates. Your certificates are listed in the details pane.
• Right-click the certificate that has your VPN server’s name, and click Open.
• On the General tab, confirm that the date listed under Valid from is today’s date. If it isn’t, you might have selected the incorrect certificate.
• On the Details tab, click Enhanced Key Usage, and verify that IP security IKE intermediate and Server Authentication are listed.
• Click OK to close the certificate.
• Close the Certificates snap-in.

Configuring NPS
• Open the NPS Console
• Right Click on “Network Policies” and select “New”
• Set the Policy name to “Always on SSTP” and the type to Remote Access Server (VPN-Dial up).
• As a condition add the user group “VPN Users”. Click Next and select “Access Granted” and click next once more.
• Deselect all checkboxes, as we want to use PEAP certificates. After deselecting click on the button “Add” and select the “Microsoft: Protected EAP (PEAP)”
• Select the “Microsot: Protected EAP (PEAP)” option and click Edit. Now select the VPN certificate we’ve installed in the previous step.
• Delete the Secured Password (EAS-MSCHap v2) Option and then click Add, now select “Smart Card or Other Certificate”
• Click Edit once more and select the VPN certificate once more.
• Now simply click next next finish and the NPS side should be all done.
Thats all for the server side. Lets go to our client test machine and configure the VPN there.
Windows Sstp Client Software
Client side
Windows Sstp Client Download
Windows Sstp Client Mac
the client is straightforward, use the following script and run it as administrator to install the VPN and have it auto-connect when it is not in the trusted network “Domain.local” The following script was supplied to me by Microsoft for create a user tunnel on SSTP with the configuration used above.
Windows Sstp Client Windows 10
Reboot or run gpupdate /force to install the user certificate that we’ve setup in our auto-enrolment policy, then execute the script.
Windows Sstp Client Windows 10
Thats it! now when you switch networks it will automatically connect to your AlwaysOn VPN. You can test this by setting your DNS to an external server such a google.com. Hope that helps!