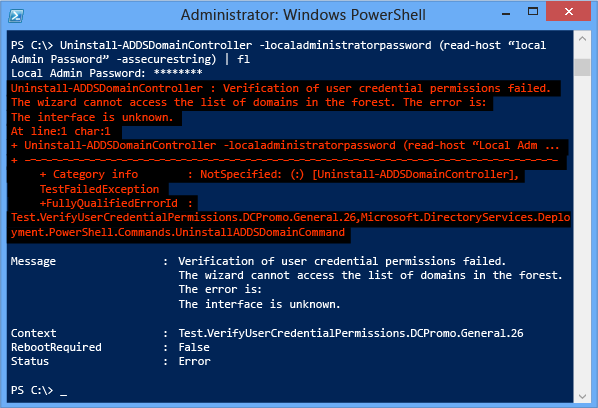
Jan 25, 2021 No DNS domain configured for freebsdtr. Unable to perform DNS Update. DNS update failed: NTSTATUSINVALIDPARAMETER 1. Nslookup mydomain.com resolved in ip addresses domain controllers from computer with NetBIOS name freebsdtr. Record on DNS server in zone mydomain.com for computer name freebsdtr not.
- Dns Update Failed: Nt Status Invalid Parameter Windows 10
- Dns Update Failed: Nt Status Invalid Parameter Password
- Net Join Dns Update Failed Nt_status_invalid_parameter
- Linux Dns Update Failed Nt_status_invalid_parameter
- Dns Update Failed Nt_status_invalid_parameter Redhat
- Jan 09, 2020 Unable to perform DNS Update. DNS update failed: NTSTATUSINVALIDPARAMETER root@terminal:# net ads join Result: Failed to join domain: failed to lookup DC info for domain 'COPICOM.LOCAL' over rpc: The attempted logon is invalid. This is either due to a bad username or authentication information. Content of /etc/hosts.
- Mar 05, 2012 DNS update failed! I found an article about how to fix this problem. The fix is to modify the 127.0.0.1 entry in the /etc/hosts file. I have mine like this: 127.0.0.1 mymachine.mycompany.com mymachine. This post may contain affiliated links. When you click on the link and purchase a product, we receive a small commision to keep us running.
serval years ago,I built freeradius server in centos 6 work with active directory. It works perfect with wifi authortication and ikev2 vpn authortication. But recently days, I found a bug that the radius server can not limit user access to a group in AD. So I’m trying to build a new freeradius server in debian 10. After a week work.At last I figure it out.
Install Software and configuration
First thing first, We need install a debian 10 server on your virtualization platform. currently, I installed a debian server on proxmox ve platform.
Basic Information
| Name | Value |
|---|---|
| Domain Name | TESTING.LOCAL |
| NTDomain Name | TESTING |
| RADIUS HOSTNAME | MYRADIUS |
| DOMAIN CONTROLLER | MYDC02.TESTING.LOCAL |
| DOMAIN CONTROLLER | MYDC03.TESTING.LOCAL |
| DOMAIN GROUP | VPN_GROUP |
Change Debian settings
- Change hostname
- Sync NTP time with domain controllerInstall chrony
restart chrony service and force update times
Install samba and winbind and let Debian Host joined domain
- Install samba,winbind,krb5-user
- config samba config file
In [global] section, change settings form

to
- Modify
/etc/nsswitch.conf
Change settings:
to
- Modify
/etc/krb5.conf
Restart OS
Join domain
Restart samba and winbind service
Testing samba AD authentication:
- Using winbind:
You will get the following message if everything is correct:
- Using ntlm_auth:
Then you will got success message:
Install freeradius
Install freeradius
Grant permission for
freeraduser on winbind’s socket:Change MACHAP to use ntlm_auth:
change
Change module mschap :
Change eap config.
Change settings of
default_eap_type.to
Then restart freeradius service
Change
/etc/freeradius/3.0/sites-enabled/defaultand/etc/freeradius/3.0/sites-enabled/inner-tunnelConfigure RADIUS client
restart service of freeradius
Test FreeRADIUS and MSCHAP:
The results will be like:
Configure freeradius-ldap Auth with AD
Dns Update Failed: Nt Status Invalid Parameter Windows 10
To limited to auth a AD group, we need to config freeradius auth with ldap.
- Install freeradius-ldap
Edit config
- edit
/etc/freeradius/3.0/mods-available/ldap
- create a link to mode-enable
- edit
/etc/freeradius/3.0/sites-available/default
- Restart freeradius service
testing ldap auth
- Change
/etc/freeradius/3.0/usersto allow specific groupVPN_GROUPof users to authenticate
- Change MACHAP to use ntlm_auth:
change
Install mysql,daloradius to make management freeradius with web access
- Install mariadb database
Renew certficiation
We purchased godaddy certification, so we will replace ssl certification
backup default eap configure file
Place pem file to
/etc/freeradius/3.0/certs/mycerts
-rw-r–r– 1 root root 1728 Feb 21 11:11 mycerts-ca.pem-rw-r–r– 1 root root 1704 Feb 21 11:09 mycerts.key-rw-r–r– 1 root root 2248 Feb 21 11:13 mycerts.pem
Modified
/etc/freeradius/3.0/mods-enabled/eapfile.
…certificate_file = /etc/freeradius/3.0/certs/vpn.grapecity.com.cn/mycerts.pem…ca-file = /etc/freeradius/3.0/certs/vpn.grapecity.com.cn/mycerts-ca.pem

Reference
The following documentation describes the process of updating Samba to a newer version.
If you want to migrate a Samba NT4 domain to Samba Active Directory (AD), see Migrating a Samba NT4 Domain to Samba AD (Classic Upgrade).
| Microsoft stopped supporting Windows NT 4.0 on December 31, 2004 and twice recently they have broken compatibility to it in Windows 10. It is probably just a matter of time until they decide not to fix a break. Samba, like Microsoft, advises upgrading to Active Directory. |
| If you update to Samba 4 and later, you do not have to migrate to Active Directory. |
The Active Directory (AD) Domain Controller (DC) support is one of the enhancements introduced in Samba 4.0. However all newer versions include the features of previous versions - including the NT4-style (classic) domain support. This means you can update a Samba 3.x NT4-style primary domain controller (PDC) to a recent version, as you previously updated, for example from 3.4.x to 3.5.x. There is no need to migrate an NT4-style domain to an AD.
Additionally, all recent versions continue to support setting up a new NT4-style PDC. The AD support in Samba 4.0 and later is optional and does not replace any of the PDC features. The Samba team understand the difficulty presented by existing LDAP structures. For that reason, there is no plan to remove the classic PDC support. Additionally we continue testing the PDC support in our continuous integration system.
Run the following steps, whether you are updating a Samba Active Directory (AD) domain controller (DC), a Samba NT4-style PDC, a Samba domain member, or a standalone installation:
- Stop all Samba services.
- Create a backup.
- Read the release notes of skipped versions. They contain important information, such as new features, changed parameter, and bug fixes. In case you switch to new major release, read the release notes of the initial version (x.y.0) and the ones from minor versions up to the new version you will update to. For example, if you update from 4.4.4 to 4.6.2, read the 4.5.0, 4.6.0, 4.6.1, and 4.6.2 release notes.
- Install the latest version over your existing one:
- If you compile Samba from the sources, use the same
configureoptions as used for your previous version. For more information, see Build Samba From the Sources.
- If you update using packages, read the distribution documentation for information how to update.
| If you update Samba by compiling from the sources, you should be aware that code can be removed for various reasons. If code is removed and you compile and install Samba over your existing Samba installation, this can lead to old libs being left on disk, this can lead to errors. For this reason, it is recommended that you replace the entire Samba installation if you compile Samba from sources. This should not affect Samba when updating by using distro packages. |
- Start Samba.
- On Samba AD DCs:
samba - On Samba NT4-style PDC/BDCs:
smbd,nmbd - On Samba domain members:
smbd,nmbdwinbind - On Samba standalone hosts:
smbd
- Check your Samba log files for errors.
- Test your updated installation.
Upgrading your AD DC's can introduce additional complications, due to things like database compatibility and managing FSMO roles. We recommend that you:
- Run the Samba AD DC database check as part of testing your updated installation.
- Refer to Updating_Multiple_Samba_Domain_Controllers for the safest way to roll out an upgrade to your DC network.
- Be aware of database compatibility when downgrading an Active Directory DC across a major release.
If you are updating Samba, always read the release notes of all versions between the previous and the one you are updating to. They contain important and additional information on new features, changed parameter options, and so on.
This section provides an overview about important changes that require your attention to fix problems of previous versions, avoid a negative performance impact, and so on.
Changes Affecting All Samba Installation Modes
File Execution Permissions
4.0.0 and later
Previously, Samba did not check the execution bit of files. As a consequence, users could execute files, such as *.exe and *.bat, on a share, even if the x-bit was not set. Samba has been enhanced and now will not execute a file if the x-bit is not set. When upgrading from a previous version, if your executable files do not have the x-bit set, you can enable the old behaviour, by setting the following parameter in individual shares or in the [global] section:
Samba Active Directory Domain Controllers
The ntvfs File Server Back End Has Been Disabled

4.5.0 and later
Previously, Samba enabled users to provision a domain controller (DC) using the ntvfs file server back end. This back end was never supported, and thus the ntvfs feature is no longer built by default in Samba 4.5.0. Consequently, starting the samba service on a DC using the ntvfs back end fails after the update and the following error is logged:
To fix the problem, migrate the file server back end on your DC to the supported s3fs back end. For details, see Migrating the ntvfs File Server Back End to s3fs.
Fixing replPropertyMetaData Attributes
4.5.0 and later
Samba versions prior to 4.5.0 stored the replPropertyMetaData attribute incorrectly. As a consequence, administrators could experience errors, such as renaming conflicts. The problem has been fixed in 4.5.0 and later versions and Samba now stores the attribute correctly. The samba-tool utility has been enhanced to detect incorrectly stored replPropertyMetaData attributes:
To fix the attributes, run:
Note that the --yes parameter automatically fixes all problems found, not just the replPropertyMetaData attributes!
You should run the check and fix operation on all Samba Domain Controllers (DC), because replPropertyMetaData is a non-replicated attribute and modifications are not replicated to other DCs.
For more information, see the Samba AD DC database check section.
Failure To Access Shares on Domain Controllers If idmap config Parameters Set in the smb.conf File
4.4.6 or later
By default, the winbindd service on a Samba Active Directory (AD) domain controller (DC) generates ID's locally on the DC and stores them in the idmap.ldb database. You can override the generated ID's by setting uidNumber and gidNumber attributes in your user accounts and groups in Active Directory. Originally, if the idmap config parameters were set in the smb.conf file they were ignored, but due to a bug in Samba 4.4.6 and later, the parameters are no longer ignored and clients fail to connect to shares on the DC. To fix the problem:
- Remove all
idmap configparameters in thesmb.conffile on DCs. - Restart the
sambaservice. - Restart the clients.
As a result, the clients will now correctly connect to shares on the DC.
New Default for LDAP Connections Requires Strong Authentication
4.4.1 or later / 4.3.7 or later / 4.2.10 or later
The security updates 4.4.1, 4.3.7 and 4.2.10 introduced a new smb.conf option for the Active Directory (AD) LDAP server to enforce strong authentication. The default for this new option ldap server require strong auth is yes and allows only simple binds over TLS encrypted connections. In consequence, external applications that connect to AD using LDAP, cannot establish a connection if they do not use or support TLS encrypted connections.
Applications connecting to Samba AD using the LDAP protocol without encryption, will display the error message:
For further information, see the 4.4.1, 4.3.7, or the 4.2.10 release notes.
AD Database Cleanup of Deleted LDAP DNS Entries
4.1.12 or later
Previously, Samba incorrectly created deleted Active Directory (AD) objects for removed DNS entries. The problem has been fixed. If you start the first Domain Controller (DC) with a fixed Samba version, all deleted objects are removed. As a result, this can result in a slow performance until the deleted objects are removed.
Incorrect TLS File Permissions
4.1.2 or later / 4.0.12 or later
Previously, Samba created the *.pem files used for LDAP TLS encryptions with insecure permissions. To avoid insecure connections, delete the files on all domain controllers (DC):
Restart Samba after you deleted the files to automatically re-create the new certificates.
Fixing Dynamic DNS Update Problems
4.0.7 or later
See Fix DNS dynamic updates in Samba versions prior 4.0.7 for details.
Fixing Incorrect Sysvol and Directory ACLs
When updating from early 4.0.x versions, 4.0 beta and 4.0 release candidates.
- To reset wrong Sysvol ACLs, run:
- To reset all well known ACLs in the directory, run:
Dns Update Failed: Nt Status Invalid Parameter Password
- To fix errors in the Active Directory (AD) database, run:
Samba Domain Members
ID Mapping Configuration Verification
4.6.0 or later
Previously, Samba did not verified the ID mapping configuration in the smb.conf file on a domain member. Thus, an incorrect ID mapping configuration could be set, such as overlapping ID ranges or incorrect back ends for the default domain. Consequently, the winbindd service started and ID mapping failed or did not work as expected. The testparm utility has been enhanced and now reports incorrect ID mapping configurations. For example:
Additionally, when using an incorrect ID mapping configuration, the winbindd service now fails to start and an error message is logged. For example:
Using Samba 4.6.0 and later, users are no longer able to use incorrect ID mapping configurations.
For further details, supported back ends on a domain member, and their configuration, see:
- the
IDENTITY MAPPING CONSIDERATIONSsection in thesmb.conf(5)man page
Net Join Dns Update Failed Nt_status_invalid_parameter
The ad ID Mapping Back End Now Supports Enabling RFC2307 or Template Mode Per-domain
4.6.0 or later
Linux Dns Update Failed Nt_status_invalid_parameter
Previously, when the winbind nss info parameter was set to rfc2307, the Samba ad ID mapping back end retrieved shell and home directory settings for all Active Directory (AD) domains from AD. In Samba 4.6.0, the new idmap config domain_name:unix_nss_info parameter has been added. This parameter enables the administrator to set on a per-AD domain basis if the shell and home directory settings of users should be retrieved from AD or if the template settings, set in the template shell and template homedir parameters are applied.
The new idmap config domain_name:unix_nss_info parameter has a higher priority than the global winbind nss info = rfc2307 setting. Therefore, using the idmap config domain_name:unix_nss_info = no default setting for an AD domain, the shell and home directory are no longer retrieved from AD and the values set in the template shell and template homedir parameters are applied. To re-enable retrieving the values from AD for a domain, set in the [global]section in your smb.conf file:
For details and an example how to set up, see idmap config ad - Configuring the ad Back End.